Describes in Detail How the Ca Uses and Manages Certificates
Hammer --fetch-ca-cert httpssatellite. The majority of CA certificates or digital certificates serve two main functions.
What Is A Certificate Authority Ca Ssl Com
Most CAs offer a SaaS platform which can be accessed 247 to manage the lifecycle of all your certificates in one place.
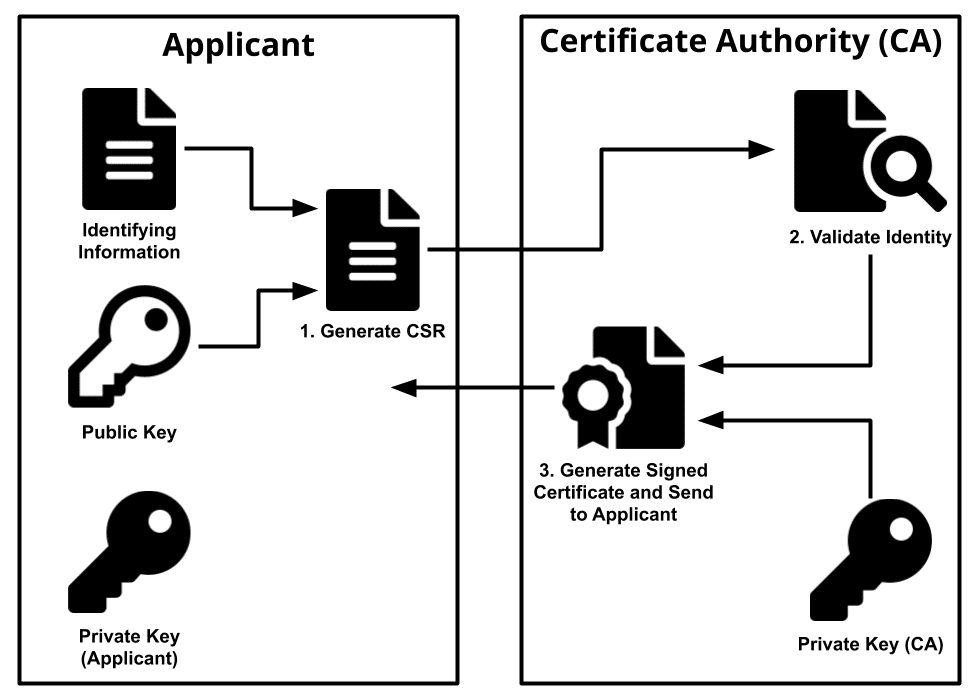
. Users interact with the Certificate Authority Web Service by accessing the CAs Web site. Certificate practice statement CPS b. A document that describes in detail how a CA uses and manages certificates as well as how end users register for a digital certificate is known as.
Encrypting the data certificates protect your private information and prevent it to be seen by the unintended recipient. This means that you can get granular reporting on all the certificates used throughout your organization no matter what application they are used for. Lifecycle policy LP d.
Certificate practice statement CPS. You may also want to change the Key Size and the Validity Period of Certificate Authority CA. Red Hat Satellite server and the CLI tool hammer work similarly but the CA certificate can be specified at the command line or in the hammercli_configyml file.
The hammer command also has an option to import the Satellite CA certificate directly into the users hammer configuration directory. A publicly accessible centralized directory that contains digital certificates that can be used to view the status of a digital certificate. Certificate practice statement CPS Certificate policy CP Lifecycle policy LP Access policy AP.
Access policy AP c. Certificate policy CP c. A document that describes in detail how a CA uses and manages certificates as well as how end users register for a digital certificate is known as.
There are several ways users can request certificates. Certificate practice statement CPS. These digital certificates are data files used to cryptographically link an entity with a public key.
A document that describes in detail how a CA uses and manages certificates as well as how end users register A document that describes in detail how a CA uses and manages certificates as well as how end users register for a digital certificate is known as Uncategorized. Asked Aug 24. You will need to fill out all the required fields in the form.
Submit and view feedback for. Definition Certificate practice statement CPS. Certificatesk8sio API uses a protocol that is similar to the ACME draft.
It verifies the identity of the applicant. A document that describes in detail how a CA uses and manages certificates as well as how end users register for a digital certificate is known as. A document that describes in detail how a CA uses and manages certificates as well as how end users register for a digital certificate is known as.
A Certification Authority to issue certificates A trusted CA is the only entity that can issue trusted digital certificates. Certificate policy CP b. The default is 1024 but this.
With digital certificates you can be ensured the entities websites companies individuals etc with whom you are interacting are really who they say they are. According to Microsoft certificate. This Local CA will be used to digitally sign local SSL certificates.
Access policy AP a. This is extremely important because while PKI manages more of the encryption side of these certificates authentication is vital to understanding which entities own what keys. Through this Web site users can request certificates view the status of a pending request.
This determines the length of the encryption key choose between 512 768 1024 2048 and 4096. A repository that lists revoked digital certificates. This allows others relying parties to rely upon signatures or on assertions made about the.
A digital certificate certifies the ownership of a public key by the named subject of the certificate. It binds a public key to an entity. The URL for the CA is usually httpscertsrv.
We will cover the most common using the Certificate Authority Web Service. A trusted third-party agency that is responsible for issuing the digital certificates. These CA and certificates can be used by your workloads to establish trust.
Question 12 A document that describes in detail how a CA uses and manages certificates as well as how end users register for a digital certificate is known as. Lifecycle policy LP d. They require minimal action or involvement from senders or recipients.
A document that describes in detail how a CA uses and manages certificates as well as how end users register for a digital certificate is known as. The digital certificate systems are also user-friendly and they usually work automatically. A document that describes in detail how a CA uses and manages certificates as well as how end users register for a digital certificate is known as.
Provides to a business that purchases one of its digital certificates. A certificate authority CA is a trusted entity that issues Secure Sockets Layer SSL certificates. A technology used to associate a users identity to a public key in which the users public key is digitally signed.
Web browsers use them to authenticate content sent from web servers ensuring trust in content delivered online. Manage TLS Certificates in a Cluster Kubernetes provides a certificatesk8sio API which lets you provision TLS certificates signed by a Certificate Authority CA that you control. With a digital certificate the authentication is privacy.
Get smart card or profile certificates. In cryptography a certificate authority or certification authority CA is an entity that issues digital certificates. In your answer describe what procedures the CA typically follows before issuing a digital certificate.
The following sections describe the certificate operations in the Microsoft Identity Manager MIM Certificate Management CM REST API.
What Is A Certificate Authority Ca And What Do They Do Hashed Out By The Ssl Store

What Is A Certificate Authority Ca Ssl Com

What Is A Certificate Authority Ca And What Do They Do Hashed Out By The Ssl Store
Comments
Post a Comment